The hack is possible, but very tricky (and unlikely)
SimpliSafe’s home security system could be prone to being fooled by a cheap trick, a new video has revealed, but it’s probably not a reason to be alarmed.
A video posted by LockPickingLawyer on YouTube demonstrates a potential vulnerability in SimpliSafe’s home security system, which could also apply to a number of wireless alarm systems.
The video shows how by using a 433 MHz remote, easily purchased online for around $2, the signal from wireless security devices to a security base station can be jammed. This could let someone open and close a door or window with a wireless contact sensor on it without triggering the alarm.
Tried and tested: SimpliSafe security system review
As noted in the video, the SimpliSafe system is capable of detecting this type of wireless interference and will notify you with a voice alert on the base station and a text message to your phone. However, as non-nefarious wireless interference is very common, it won’t trigger the alarm or alert the monitoring station. If you have cameras in your monitored SimpliSafe system, interference will trigger video recording. This means it’s important to check on your home if you receive one of these wireless interference text message alerts.
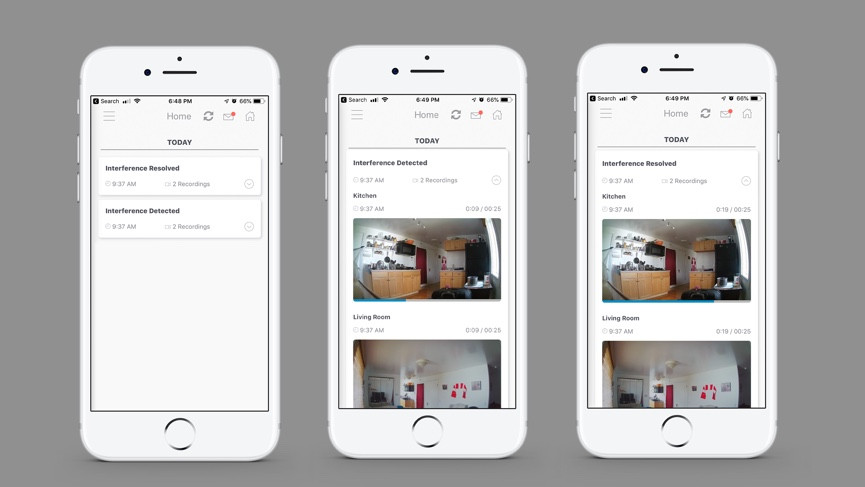
SimpliSafe responded to the video with a statement saying that while what it demonstrates is possible, the number of variables in the real world required to make this hack work are such that it is very unlikely to be replicated.
“In this video, the videomaker finds a precise frequency, signal strength, and orientation of system components in which they can thread the needle of blocking system communication without triggering an alert,” the company told us. “In real life, this is unlikely. Because signal strength degrades unpredictably depending on distance and landscape, it would be very difficult for anyone to hit on the ‘right’ strength without triggering an alert.”
SimpliSafe also points out that a potential intruder would need to know where the motion sensors, door sensors, and base station were located in the home to be able to select a signal strength that will both jam and not be detected.
The company did say that it regularly releases security and usability updates that make it increasingly difficult for anyone to use this type of attack. “We are in the process of another round of detection algorithm tuning, which will continue to refine our ability to differentiate between brief interference noise and bad actors. This update is currently in beta and will be released remotely in a month or so,” the company told The Ambient.
While again that means it’s still possible, it’s also worth remembering that research shows criminals are more likely to take the easy route, and while signal jamming may be simpler than other forms of computer hacking, it’s still more difficult than breaking a window or forcing a door – both of which would be detected by a wireless home security system.